|
Procurement Sensitive/Pre-Decisional - Do Not Distribute |
|
|
|
|
|
|
For Reference: |
|
|
|
|
|
|
|
FedRAMP High Baseline Controls (Opens a new Excel) |
|
|
|
|
|
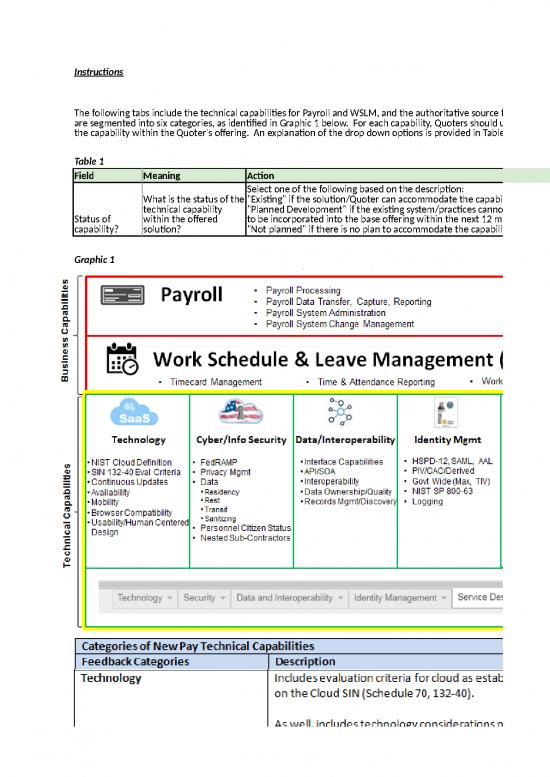
Security Capabilities |
|
|
|
|
|
|
ID |
Capability |
Authoritative Reference |
Acquisition Team Recommendation |
Status of capability? |
Comments |
|
Confused at if we have FEDRamp Assessment and a tab here for FEDRamp. Seems repetitive +stephanie.hrin@gsa.gov +peggy.martin@gsa.gov
-Raymond McCollum - QT2F1BA
SOO FedRAMP Requirements |
|
|
|
|
|
|
SC-01 |
Obtains, within 1 year of award and continuously maintains throughout performance period as baseline changes occur, authorization through FedRAMP High and/or Medium baseline and complies with related requirements as mandated by Federal laws and policies, including availability of documentation, physical access, and logical access needed to support this requirement.
FedRAMP High Baseline Controls
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/482/2016/07/FedRAMP-High-HHH-Baseline-Controls-2016-05-18.xlsx
FedRAMP Moderate Baseline Controls
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/482/2016/07/FedRAMP-Moderate-HHH-Baseline-Controls-2016-05-18.xlsx |
FedRAMP Guidance |
|
|
|
|
SC-03 |
Complies with the FedRAMP standard contract clauses.
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/482/2015/03/FedRAMP_Standard_Contractual_Clauses_062712_0.pdf |
FedRAMP Guidance
Industry Best Practice/Gartner |
|
|
|
|
Other SOO Requirements |
|
|
|
|
|
|
SC-05
|
Results of security assessments throughout full life cycle are available to the Authorizing Official for review and further action. (CA-2) |
NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems
|
|
|
|
|
SC-06
|
Throughout performance lifecycle, where the Quoter does not currently meet included security services objectives, a Security Gap Mitigation Plan that contains the series of steps to adjust technologies and/or procedures to ensure a sufficiently secure environment. |
NIST SP 800-30 Guide to Conducting Risk Assessments |
|
|
|
|
SC-07
|
SaaS Quoter uses standard contract terms for addressing disciplinary action, consistent with the Federal Acquisition Regulations in all contracts that permit contractor employees access to information and information systems containing Federal data. |
3.1 Improper Business Practices and Personal Conflicts of Interest -- Safeguards
3.11 Improper Business Practices and Personal Conflicts of Interest -- Preventing Personal Conflicts of Interest for Contractor Employees Performing Acquisition Functions
9.4 Contractor Qualifications -- Debarment, Suspension, and Ineligibility
52.2 Solicitation Provisions and Contract Clauses -- Text of Provisions and Clauses |
Contract Dispute Act |
|
|
|
SC-08
|
Provides notification to all appropriate Government personnel (e.g., Chief Counsel, Human Resources, Personnel) at Task Order issuing agencies within a period of time deemed appropriate at task order level if a formal employee sanctions process is initiated on staff with access to Federal data, identifying the individual sanctioned and the reason for the sanction. |
NIST SP 800-61 Computer Incident Handling Guide |
|
|
|
|
SC-10
|
Do we need to put this one here, since we already stated that they must have the ability to obtain and maintain FedRamp?
-Raymond McCollum - QT2F1BA
Ensures contracts with external companies for repair or recovery of data from systems, hard drives, or media require a non-disclosure statement. In cases where external companies provide non-local (e.g., external, remote access to SaaS Quoter systems, hard drives, or media) maintenance, repair, or data recovery, the contract with the external company shall also include provisions to require: (a.) cryptographic mechanisms to protect the integrity and confidentiality of communications; (b.) use of strong authenticators in the establishment of nonlocal maintenance and diagnostic sessions; and, (c.) services are to be performed from an information system that implements a security capability comparable to the capability implemented on the system being serviced. |
NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems |
|
|
|
|
SC-12
|
We're asking for a document here. This should be removed. If we allow the quoters to have slides during the oral presentation, then this can be included. It's already a factor under oral presentations.
-Raymond McCollum - QT2F1BA
Able to identify staff and contractors of SaaS provider with access to audit logs, as requested by government. |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems |
|
|
|
|
SC-13 |
When forming agreements with entities outside the SaaS Provider for operation and maintenance of SaaS provider-owned IT systems, Quoters include in the agreement language addressing responsibility for Risk Management Framework activities and access to Security Assessment and Authorization documentation. |
NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems |
|
|
|
|
SC-14 |
Reporting to Government Contracting Officer and Government Authorizing Official of suspected loss or compromise of the private keys to the SaaS solution incident response team in accordance with reporting thresholds in task order requirements. |
NIST SP 800-32 Introduction to Public Key Technology and the Federal PKI Infrastructure
NIST 800-61 Computer Security Incident Handling Guide |
|
|
|
|
Security Operations Capabilities |
|
|
|
|
|
|
SC-15
|
Locate all data centers, all data and backup facilities in the United States of America. |
FedRAMP Contract Clauses
NIST SP 800-122 |
|
|
|
|
SC-16 |
Documents annually, interconnections between external networks, including third party providers, with an Interconnection Security Agreement (ISA) signed by both the SaaS Quoter and Agency Authorizing Officials. |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems
NIST SP 800-47 Security Guide for Interconnecting Information Technology Systems |
|
|
|
|
SC-17
|
Uses continuous monitoring capabilities for traffic between the SaaS Quoter and a Federal agency that passes through one or more cloud service gateways or Cloud Access Service Broker (CASB). |
NIST SP 800-137 Information Security Continuous Monitoring (ISCM) for Federal Information Systems and Organizations |
|
|
|
|
SC-18
|
Sanitizes data residing on all media being refreshed in accordance with NIST Special Publications 800-88'Guidelines for Media Sanitization, in the event of hardware refresh and replacement. |
NIST SP 800-88 Guidelines for Media Sanitization |
|
|
|
|
SC-19
|
Maintains action logs available to government points of contacts for the SaaS solution. |
NIST 800-92 Guide to Computer Security Log Management |
|
|
|
|
SC-20
|
Performs manual or automated audits, scans, reviews, or other inspections. |
NIST SP 800-115 Technical Guide to Information Security Testing and Assessment. |
|
|
|
|
SC-21
|
Accomodates govt request to run application vulnerability scans within notification guidelines stipulated in Task Order requirements.
|
NIST SP 800-115 Technical Guide to Information Security Testing and Assessment. |
|
|
|
|
SC-22
|
Provides 48 hour notice of planned Quoter penetration testing to Task Order issuing agencies. |
NIST SP 800-115 Technical Guide to Information Security Testing and Assessment. |
|
|
|
|
SC-23 |
Tracks and mitigates issues across functional, cybersecurity, accessibility, integration, service and other areas in coordination with the government. |
NIST SP 800-61, Revision 2 Computer Security Incident Handling Guide"
US-CERT Incident Notification Guidelines
https://www.us-cert.gov/incident-notification-guidelines |
|
|
|
|
SC-24 |
Provides investigation support to government security personnel or third party investigative support services as part of the breach policy and process. |
NIST SP 800-61 Computer Security Incident Handling Guide
Industry Best Practice/Gartner Recommendation |
|
|
|
|
SC-26 |
Uses SSL/TLS as the encryption mechanism of choice in user interface, API, batch import/export, and other secure connections and is able to comport to task order issuing agency requirements. |
M-15-13, Policy to Secure Connections Across Federal Web Sites and Web Services
https://https.cio.gov/ |
|
|
|
|
Systems and Services Acquisition Capabilities |
|
|
|
|
|
SC-27 |
Access to source code available to vendor staff and contractors physically located in the U.S. who are U.S. Citizens or maintain lawful permanent resident status. |
NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems |
|
|
|
|
SC-28 |
When implementing IP connections on CSP perimeter firewalls, only services that are required shall be permitted (to pass through a firewall). For each permitted service, this information shall be documented:
i. Service allowed (including TCP or UDP port number);
ii. Service description;
iii. Business case necessitating the service; and
iv. Internal controls associated with the service. |
NIS 800-53 Security and Privacy Controls for Federal Information Systems |
|
|
|
|
SC-29 |
When implementing IP connections on SaaS solution perimeter firewalls, inbound filtering is performed to exclude or reject all data packets that have an internal host address. Inbound filtering is implemented in accordance with NIST SP 800-41, Section 4.2, Implementing a Firewall Rule Set. |
NIST 800-41 Guidelines on Firewalls and Firewall Policy |
|
|
|
|
SC-30 |
Network and system protocols running on Quoter's network are most recent version when they do not negatively impact availability. A risk based decision used to determine when it is appropriate to implement older protocols with notification to government. |
NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems |
|
|
|
|
SC-31 |
Emerging technology products are assessed to determine potential threats when introduced into the SaaS infrastructure. As technology continues to evolve, SaaS Provider ensure these threats continue to be analyzed. |
NIST SP 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems |
|
|
|
|
System and Information Integrity Capabilities |
|
|
|
|
|
SC-32 |
Integrity verification tools are employed to detect unauthorized changes to system kernels, drivers, firmware (e.g., BIOS), software (e.g., OS, applications, middleware) and security attributes. |
NIST 800-53 Security and Privacy Controls for Federal Information Systems |
|
|
|
|
SC-33 |
Protects confidentiality of controlled unclassified information (CUI) at FIPS 140-2 Level 1. |
Executive Order 13556 Controlled Unclassified Information
NIST SP 800-171 Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations |
|
|
|
|
SC-34 |
The SaaS solution shall incorporate the detection of the following into the SaaS solution’ incident response capability: (SI-7 CE7)
• Unauthorized changes to baseline configuration setting
• Unauthorized elevation of system privileges |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems
NIST SP 800-32 Introduction to Public Key Technology and the Federal PKI Infrastructure |
|
|
|
|
SC-35 |
Quoters will report data related to security configuration and vulnerability management, in accordance with processes and mechanisms as may be established by task order issuing agency. |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems
|
|
|
|
|
SC-36 |
Once the incident handling has been completed, the following actions shall be performed by the SaaS solution:
a) Notifying the affected Authorizing Official of actions taken and changes made to systems/applications affecting their SaaS instance.
b) Changes made to systems and applications are reviewed, in accordance with the agency's auditing and incident response procedures, to determine if they are still relevant.
c) Request any actions to undo changes through the existing configuration management processes.
d) Document and control any changes remaining as part of normal configuration management processes. |
NIST SP 800-184 Guide for Cybersecurity Event Recovery |
|
|
|
|
SC-37 |
Published plan for for key management. Should key escrow exist, applicable terms and conditions of escrow apply for retrieving encrypted information will be included in the key management plan |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems
NIST SP 800-152 A Profile for U.S. Federal Cryptographic Key Management Systems
NIST SP 800-32 Introduction to Public Key Technology and the Federal PKI Infrastructure |
|
|
|
|
Privacy Controls Capabilities |
|
|
|
|
|
SC-38 |
The solution is compliant with the Privacy Act of 1974 and related PII requirements ensuring conformance to privacy information maintenance requirements, protecting against unauthorized disclosure, developing and maintaining an accounting of disclosures from any Privacy Act system operated by the SaaS Quoter. |
Privacy Act of 1974
M-10-23: Guidance for Agency Use of Third-Party Websites and Applications
NIST 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
|
|
|
|
|
SC-39 |
SaaS Provider coordinates with Federal agency in the development and updating of Privacy Impact Assessment and System of Record Notice in accordance with Section 208 of the e-government Act. |
eGovernment Act 2002, Section 208 |
|
|
|
|
SC-40 |
SaaS Provider regularly assesses and reports to task order issuing agencies effectiveness of management, operational and technical privacy controls to protect the assured, proper, and consistent collection, processing, communication, use and disposition of personal information (PI) and personally identifiable information (PII).
|
Related NIST 800-53 Privacy Controls: AR-1: Governance and Privacy Program, AR-2: Privacy Impact and Risk Assessment, AR-3: Privacy Requirements for Contractors and Service Providers, AR-4: Privacy Monitoring and Auditing, AR-6: Privacy Reporting, AR-8: Accounting of Disclosures.
|
|
|
|
|
SC-41 |
Privacy practices, policies and processes ensure obtainment of individuals’ consent prior to the collection or other use of their PII to the greatest extent practicable. |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
|
|
|
|
|
SC-42 |
An active corporate privacy program exists that uses information on Information Privacy training from the government for its personnel. |
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
NIST SP 800-50 Building an Information Technology Awareness and Training Program |
|
|
|
|
SC-43 |
Access to PII is provided only to employees, contractors, and other entities which require specific PII for legitimate business functions in support of their official duties with personnel signing NDA where appropriate.
|
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII)
|
|
|
|
|
SC-44 |
SaaS Provider is HIPAA compliant to extent applicable by law within the context of payroll processing. |
Health Insurance Portability and Accountability Act of 1996 |
|
|
|
|
SC-45 |
Maintains an accurate accounting of disclosures of PII including: date, nature, and purpose of each disclosure; and the name and address of the person or entity to which the disclosure was made |
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII) |
|
|
|
|
SC-46 |
Includes Privacy Act Statements on the forms or pages that collect PII.
|
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII) |
|
|
|
|
SC-47 |
Uses personally identifiable information (PII) internally only for the authorized purpose(s) identified in the Privacy Act and/or in public notices.
|
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII) |
|
|
|
|
SC-48 |
The system discloses PII externally only for the authorized purposes identified in the Privacy Act and/or described in its notice(s) or for a purpose that is compatible with those purposes.
|
NIST SP 800-53 Security and Privacy Controls for Federal Information Systems and Organizations
NIST SP 800-122 Guide to Protecting the Confidentiality of Personally Identifiable Information (PII) |
|
|
|
|
SC-049 |
Access to payroll and WSLM data available to staff and contractors physically located in the U.S. who are U.S. Citizens or maintain lawful permanent resident status. |
|
|
|
|
|
SC-050 |
SaaS Quoter provides visibility into 3rd party dependencies.
-Inventorying active partnerships with partner Quoters with access to Federal data or builds services that would access to Federal data.
-Provides visibility to Task order issuing agency of contract terms/conditions with 3rd party partners providing system repair, recovery, and disposal services or any other system containing or accessing Federal data.
-Holds subscontractor and third party Quoters to equivalent staadards of compliance as held to by the government. |
|
|
|
|
|
Procurement Sensitive/Pre-Decisional - Do Not Distribute |
|
|
|
|
|
|
|
|
|
|
Technology Capabilities |
|
|
|
|
|
|
|
|
|
|
ID |
Capability |
Authoritative Reference |
Additional Information |
Status of capability? |
Comments |
|
|
|
|
|
Cloud Computing (132-40 SIN) |
|
|
|
|
|
|
|
|
|
|
Contract Requirements |
|
|
|
|
|
|
|
|
|
|
TR-000 |
Credentials for all master accounts that can enable provisioning of agency users shall be held by task order issuing agency.
-Reseller shall not hold access to master accounts as a vector for unauthorized access to agency private data.
-Resellers shall not have ability to access data operating within SaaS service at any time.
-All SaaS accounts can be transferred, at no charge, to another reseller or directly to task order issuing agency at the end of the contract term.
-Resellers may not claim intellectual property rights to any account configurations established by reseller for agencies under the contract in any way that would prevent a seemless, no cost transfer of the SaaS accounts at end of term. |
Agency feedback |
|
|
|
|
|
|
|
|
TR-001 |
Establish the Quoter's SaaS product on the Schedule 70 Cloud Computing SIN (132-40), and in the SaaS Sub-Category by the time of Award. |
Response Guidance and Checklist for IT Schedule 70 Holders to Add Cloud Computing Services SIN (132-40)
https://www.gsa.gov/portal/getMediaData?mediaId=130366 |
Quoters may submit a contract modification to add their service to Schedule 70, SIN 132-40, SaaS Sub-Category in parallel to the BPA proposal submission process. |
|
|
|
|
|
|
|
Other SOO Requirements |
|
|
|
|
|
|
|
|
|
|
TR-002 |
Coordinates with customer community at appropriate stages for releases of new software versions including testing integration and usability. |
NIST SP 800-128 Guide for Security-Focused Configuration Management of Information Systems
NIST SP 800-64 Security Considerations in the System Development Life Cycle |
|
|
|
|
|
|
|
|
TR-003 |
Continuously modernizes capabilities over time as technology advances in the marketplace.
Examples of emerging capabilities range from but are not limited to robotic process automation, artificial intelligence, analytics and machine learning to routine advances in browser capability, responsive design, mobility, and progress made in cybersecurity and cloud computing technologies
|
Industry Best Practice |
|
|
|
|
|
|
|
|
TR-004 |
Solution is extensible through methods such as configuration, add-ons, etc. |
You have two requirements in cell c20. Break apart. Keep Garnter rec. Compliance w/ NIST def of cloud takes care of the other req.
-Kermit McKelvy - QT3KAB
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
TR-005 |
Capability to provide developers programs that build skills and validate expertise in the labor market through learning opportunities, testing, and/or certification of developers, administrators, or business users. |
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
Other Technical Capabilities |
|
|
|
|
|
|
|
|
|
|
Hosting Capabilities |
|
|
|
|
|
|
|
|
|
|
TR-006 |
Distributes all data center locations within the United States of America, ensures independence and/or interdependence sufficiently meet full spectrum of natural and man-made continuity of operations (COOP) scenarios.
|
NIST SP 800-34 Contingency Planning Guide for Federal Information Systems |
|
|
|
|
|
|
|
|
TR-007 |
Publishes usage metrics so customers understand key information such as standard performance and usage information or that may affect billing such as users, storage, transactions processed, etc. |
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
TR-008 |
Ensures system failover is transparent to end users and maintains full functionality. |
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
TR-009 |
Availability of development, test, and/or staging instances for purposes included but not limited to pre-release testing, microservice, integration, and API development, training, & feedback. |
NIST SP 800-64 Security Considerations in the System Development Life Cycle
NIST Publication "The System Development Life Cycle"
http://ws680.nist.gov/publication/get_pdf.cfm?pub_id=902622 |
|
|
|
|
|
|
|
|
TR-010 |
Enables government to perform latency testing of SaaS from government connection with appropriate notification and provides customer-facing version of internal performance testing results. Performance and latency testing shall include both user interface, business logic, mobile apps, plug-ins, and API functionality. |
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
TR-011 |
This is part of the FedRAMP requirement.
-Kermit McKelvy - QT3KAB
Offers availability of SaaS 99.9% of time to Federal agencies, notwithstanding planned outages.
|
NIST SP 800-145 Cloud Computing Synopsis and Recommendations |
Acceptable downtime as a result of planned outages shall be determined on a task order basis. |
|
|
|
|
|
|
|
TR-012 |
Monitors real time performance of the SaaS solution and with customer defined alerting thresholds as specified in task order requirements. |
NIST SP 800-14 Generally Accepted Principles and Practices for Securing Information Technology Systems |
|
|
|
|
|
|
|
|
TR-013 |
Is compatible with desktop and mobile web browsers including at least three but not necessarily limited to the following options:
-Microsoft Internet Explorer
-Google Chrome
-Apple Safari
-Mozilla Firefox (+ESR)
-Microsoft Edge
Continue SaaS compatibility for these browser variations through their supportable lifespan as defined by OEM Quoters (Microsoft, Google, Apple, etc.). |
United States Government Configuration Baseline
https://usgcb.nist.gov/index.html |
|
|
|
|
|
|
|
|
TR-014 |
Enhances software functionality at least semi-annually and in response to directives flagged and agreed to by overall customer community as requiring more responsive releases that improve functionality, address issues, and increase usability. |
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
TR-015 |
Generates documents in standards based formats with a preference for PDF, HTML, and formats specified by task order issuing agencies. |
Industry Best Practice / Gartner Recommendation |
|
|
|
|
|
|
|
|
TR-016 |
Secure email messages sent from the system, and provide formatting compatible with email clients in use by Federal government (plain text, HTML, etc.) |
NIST SP 800-45 Guidelines on Electronic Mail Security |
|
|
|
|
|
|
|
|
Mobile Computing Capabilities |
|
|
|
|
|
|
|
|
|
|
TR-017 |
Provides SaaS solution functions on mobile devices such as smart phones and tablets through either a browser or native mobile app in a manner that comports to FIPS 140-2 requirements. |
NIST SP 500-316 Framework for Cloud Usability
Government Use of Mobile Technology
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Government_Mobile_Technology_Barriers_Opportunities_and_Gaps.pdf |
|
|
|
|
|
|
|
|
TR-018 |
Renders Mobile versions of web interface through a responsive design appropriate to mobile phones and tablets. |
NIST SP 500-316 Framework for Cloud Usability
Government Use of Mobile Technology
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Government_Mobile_Technology_Barriers_Opportunities_and_Gaps.pdf |
|
|
|
|
|
|
|
|
TR-019 |
Enables end user, self-service, and, optionally, administrative aspects of its mobile experiences featureset. |
NIST SP 500-316 Framework for Cloud Usability
Government Use of Mobile Technology
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Government_Mobile_Technology_Barriers_Opportunities_and_Gaps.pdf |
|
|
|
|
|
|
|
|
TR-020 |
Compatible mobile apps available for the provider's SaaS function with major Mobile Device Management platforms. |
NIST SP 500-316 Framework for Cloud Usability
NIST SP 800-124 Guidelines for Managing the Security of Mobile Devices in the Enterprise
Government Use of Mobile Technology
https://s3.amazonaws.com/sitesusa/wp-content/uploads/sites/1151/2016/10/Government_Mobile_Technology_Barriers_Opportunities_and_Gaps.pdf |
|
|
|
|
|
|
|
|
User Experience Capabilities |
|
|
|
|
|
|
|
|
|
|
TR-021 |
Provides human-centered design, focused on positive user experience. |
See usability.gov for guidelines and standards |
Can I delete this? I'm planning to delete this column
-stephanie.hrin
Yes - deleting now across all the sheets. Thanks
-Robert Wuhrman - M1Z
|
|
|
|
|
|
|
|
TR-022 |
Allows for re-labeling of fieldnames in user interface to provide for meaningful and descriptive labels. |
Usability.gov, Chapter 9, Headings, Titles, and Labels |
|
|
|
|
|
|
|