310x Filetype XLSX File size 0.09 MB Source: snapshot.ict.govt.nz
Sheet 1: Index and Descriptions
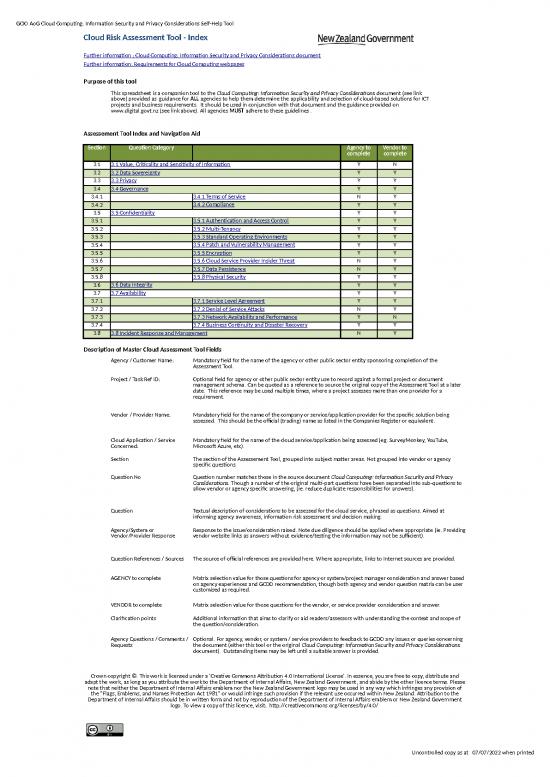
| Cloud Risk Assessment Tool - Index | ||||||
| Further information : Cloud Computing: Information Security and Privacy Considerations document | ||||||
| Further information: Requirements for Cloud Computing webpages | ||||||
| Purpose of this tool | ||||||
| This spreadsheet is a companion tool to the Cloud Computing: Information Security and Privacy Considerations document (see link above) provided as guidance for ALL agencies to help them determine the applicability and selection of cloud-based solutions for ICT projects and business requirements. It should be used in conjunction with that document and the guidance provided on www.digital.govt.nz (see link above). All agencies MUST adhere to these guidelines . | ||||||
| Assessement Tool Index and Navigation Aid | ||||||
| Section | Question Category | Agency to complete | Vendor to complete | |||
| 3.1 | 3.1 Value, Criticality and Sensitivity of Information | Y | N | |||
| 3.2 | 3.2 Data Sovereignty | Y | Y | |||
| 3.3 | 3.3 Privacy | Y | Y | |||
| 3.4 | 3.4 Governance | Y | Y | |||
| 3.4.1 | 3.4.1 Terms of Service | N | Y | |||
| 3.4.2 | 3.4.2 Compliance | Y | Y | |||
| 3.5 | 3.5 Confidentiality | Y | Y | |||
| 3.5.1 | 3.5.1 Authentication and Access Control | Y | Y | |||
| 3.5.2 | 3.5.2 Multi-Tenancy | Y | Y | |||
| 3.5.3 | 3.5.3 Standard Operating Environments | Y | Y | |||
| 3.5.4 | 3.5.4 Patch and Vulnerability Management | Y | Y | |||
| 3.5.5 | 3.5.5 Encryption | Y | Y | |||
| 3.5.6 | 3.5.6 Cloud Service Provider Insider Threat | N | Y | |||
| 3.5.7 | 3.5.7 Data Persistence | N | Y | |||
| 3.5.8 | 3.5.8 Physical Security | Y | Y | |||
| 3.6 | 3.6 Data Integrity | Y | Y | |||
| 3.7 | 3.7 Availability | Y | Y | |||
| 3.7.1 | 3.7.1 Service Level Agreement | Y | Y | |||
| 3.7.2 | 3.7.2 Denial of Service Attacks | N | Y | |||
| 3.7.3 | 3.7.3 Network Availability and Performance | Y | N | |||
| 3.7.4 | 3.7.4 Business Continuity and Disaster Recovery | Y | Y | |||
| 3.8 | 3.8 Incident Response and Management | N | Y | |||
| Description of Master Cloud Assessment Tool Fields | ||||||
| Agency / Customer Name: | Mandatory field for the name of the agency or other public sector entity sponsoring completion of the Assessment Tool. | |||||
| Project / Task Ref ID: | Optional field for agency or other public sector entity use to record against a formal project or document management schema. Can be quoted as a reference to source the original copy of the Assessment Tool at a later date. This reference may be used multiple times, where a project assesses more than one provider for a requirement. | |||||
| Vendor / Provider Name: | Mandatory field for the name of the company or service/application provider for the specific solution being assessed. This should be the official (trading) name as listed in the Companies Register or equivalent. | |||||
| Cloud Application / Service Concerned: | Mandatory field for the name of the cloud service/application being assessed (eg. SurveyMonkey, YouTube, Microsoft Azure, etc). | |||||
| Section | The section of the Assessement Tool, grouped into subject matter areas. Not grouped into vendor or agency specific questions. | |||||
| Question No | Question number matches those in the source document Cloud Computing: Information Security and Privacy Considerations. Though a number of the original multi-part questions have been separated into sub-questions to allow vendor or agency specific answering, (ie. reduce duplicate responsibilities for answers). | |||||
| Question | Textual description of considerations to be assessed for the cloud service, phrased as questions. Aimed at informing agency awareness, information risk assessment and decision making. | |||||
| Agency/System or Vendor/Provider Response | Response to the issue/consideration raised. Note due diligence should be applied where appropriate (ie. Providing vendor website links as answers without evidence/testing the information may not be sufficient). | |||||
| Question References / Sources | The source of official references are provided here. Where appropriate, links to Internet sources are provided. | |||||
| AGENCY to complete | Matrix selection value for those questions for agency or system/project manager consideration and answer based on agency experiences and GCDO recommendation, though both agency and vendor question matrix can be user customised as required. | |||||
| VENDOR to complete | Matrix selection value for those questions for the vendor, or service provider consideration and answer. | |||||
| Clarification points | Additional information that aims to clarify or aid readers/assessors with understanding the context and scope of the question/consideration. | |||||
| Agency Questions / Comments / Requests | Optional. For agency, vendor, or system / service providers to feedback to GCDO any issues or queries concerning the document (either this tool or the original Cloud Computing: Information Security and Privacy Considerations document). Outstanding items may be left until a suitable answer is provided. | |||||
| Crown copyright ©. This work is licensed under a 'Creative Commons Attribution 4.0 International License'. In essence, you are free to copy, distribute and adapt the work, as long as you attribute the work to the Department of Internal Affairs, New Zealand Government, and abide by the other licence terms. Please note that neither the Department of Internal Affairs emblem nor the New Zealand Government logo may be used in any way which infringes any provision of the "Flags, Emblems, and Names Protection Act 1981" or would infringe such provision if the relevant use occurred within New Zealand. Attribution to the Department of Internal Affairs should be in written form and not by reproduction of the Department of Internal Affairs emblem or New Zealand Government logo. To view a copy of this licence, visit: http://creativecommons.org/licenses/by/4.0/ | ||||||
| Cloud Risk Assessment Tool - Instructions | ||||||
| Further information : Cloud Computing: Information Security and Privacy Considerations document | ||||||
| Further information: Requirements for Cloud Computing webpages | ||||||
| All public cloud computing decisions need to be made in the context of an enterprise-wide ICT assurance view. In the first instance, agencies are expected to adopt Government ICT Common Capabilities if they exist. | ||||||
| This guidance must be followed for all cloud services including new services, Government ICT Common Capabilities, continuation of services and contract renewals. Read the guidance on www.ict.govt.nz (see the link above) regarding the Cloud Computing: Information Security and Privacy Considerations (see the link above) prior to using this tool. | ||||||
| This Cloud Risk Assessment Tool is a replication of the questions in the Cloud Computing: Information Security and Privacy Considerations document (see link above). It is intended to be used in support of the Cloud Service Requirements process chart, though agencies can also use it in support of their own project requirements and processes as appropriate. This tool is designed to assist agencies in collecting the relevant information that will subsequently inform the risk assessment stage of any cloud services selection. | ||||||
| Agencies are to inform GCDO when they use this tool to assess cloud services. The GCDO Government Enterprise Architecture team can provide guidance on the tools application. Refer also to the Cloud Service Requirements chart for further guidance. | ||||||
| It is expected that agencies will conduct an initial information valuation by completing the first three sections (Questions 1-27) of this Cloud Risk Assessment Tool. This information will assist agencies in understanding the 'information value' to be invested in the target service, notably: | ||||||
| Ø The classification of the information concerned. | ||||||
| Ø The confidentiality, integrity and availability of the information concerned. | ||||||
| Ø The presence of Personally Identifiable Information (PII) - to identify if a Privacy Information Assessment (PIA) is required. | ||||||
| Ø Sovereignty, commercial, financial or reputational risks. | ||||||
| Dependent upon analysis of the results of the initial agency questions (Questions 1-27) concerning the information/data to be stored, handled and transiting the proposed cloud-based solution, complete the remaining sections of this Cloud Risk Assessment Tool appropriately (ie. no questions should be ignored, though a number may not be relevant to a particular set of requirements). | ||||||
| Several cloud service vendors have developed standard response documents for the Cloud Computing: Information Security and Privacy Considerations, which can be provided to government agencies upon request. Agencies should approach potential cloud vendors when conducting this assesment. | ||||||
| The GCDO will review the contents of this tool and associated guidance on an ongoing basis, using the results of agencies cloud assessments and direct feedback. Please submit comments and change requests to GCDO. | ||||||
| Version: | v1.1.1 (15 Sep 15). Corrections and minor amendments from v1.1. | |||||
| Author: | Phil Cutforth MBE MSc, AoG Enterprise Architect, DIA SST | |||||
| Contributors / Reviewers: | GCDO thanks Industry suppliers and agencies who have contributed to the development and review of this tool. | |||||
| Contact Us: | For any questions and suggestions for amendments or improvements, email the GCDO team at: | |||||
| GCDO@dia.govt.nz | ||||||
| Master Document: | Cloud Computing: Information Security and Privacy Considerations document | |||||
| Licence: | Crown copyright ©. This work is licensed under a Creative Commons Attribution 4.0 International License. In essence, you are free to copy, distribute and adapt the work, as long as you attribute the work to the Department of Internal Affairs, New Zealand Government, and abide by the other licence terms. Please note that neither the Department of Internal Affairs emblem nor the New Zealand Government logo may be used in any way which infringes any provision of the "Flags, Emblems, and Names Protection Act 1981" or would infringe such provision if the relevant use occurred within New Zealand. Attribution to the Department of Internal Affairs should be in written form and not by reproduction of the Department of Internal Affairs emblem or New Zealand Government logo. To view a copy of this licence, visit: http://creativecommons.org/licenses/by/4.0/ | |||||
no reviews yet
Please Login to review.